Hacking passwords(without brute force)
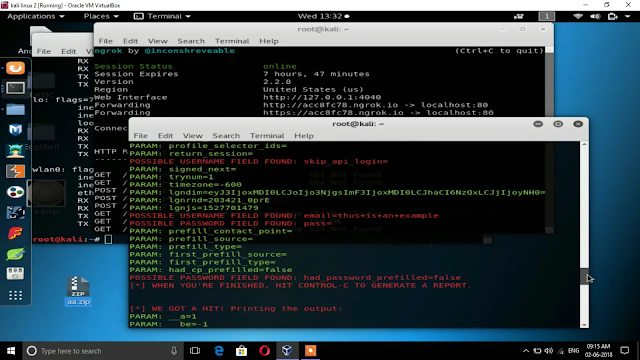
FOR VIDEO CLICK HERE Check out the above video for demonstration of this hack. This blog or me is not responsible for any illegal action performed. The above hack is performed with permissions. So Let's start hacking: Step 1) Fire up kali linux and install ngrok and setoolkit To install ngrok *goto the official ngrok website and download the zip file after downloading open terminal and type Unzip filename.zio and then Mv ngrok /usr/bin To install setoolkit *open terminal and type Git clone (git hub setoolkit address) Step 2) After installing ngrok type ngrok http 80 Output: Step 3) Now open setoolkit by typing Setoolkit ...





